For those of you who are looking to start running a .onion service, you might find this article interesting. If you've seen the services links the hidden wiki has and you think you can bring something new or better to the table but you need to protect your identity then you must create a .onion service.
Obviously everything is graviting arround the TOR network so first you need to install Tor browser from their website, it's available for Windows, Mac OS, Linux and even android but we will be focusing on the Linux option as it's the safest out of them all.
Let's install it from the Linux terminal by typing the following :
~$ sudo apt install torbrowser-launcher
Wait for tor to be installed on your machine and when it's completed let's try to browse a hidden service. Open the browser and it will connect to the network , you might need to click on the ,,connect'' button for that to happend the first time you start it. Try one of the onion websites from our hidden wiki link list.
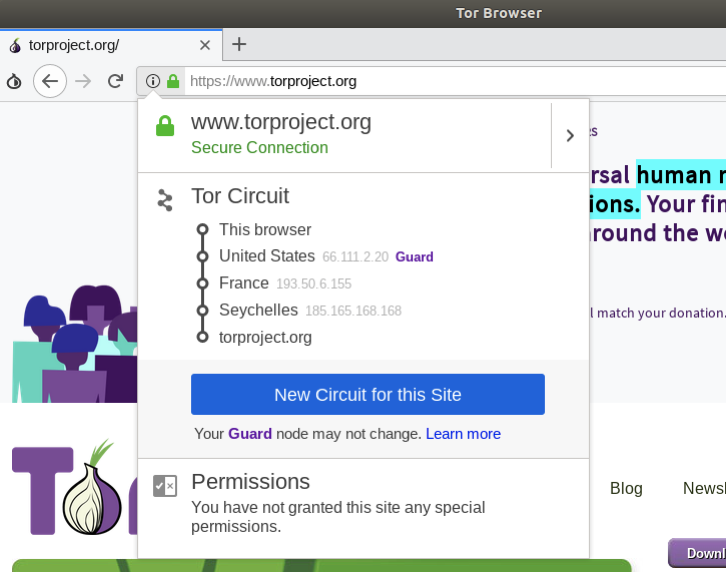
On the latest versions of the browser you can see the circuit making the connection possible, you can see the relays your connection is tied to by clicking on the small relay icon at the begining of the domain address.

If you managed to browser a few hidden services you must get to more serious things and the next step is to host your service at a host and here are a few hosting companies taking crypto payments for their services :
Once you paid your hosting and they e-mailed you the access details to the server it's time to get it set up and the first step is to configure Tor server and for that you can follow this well explained guide.
That was the hardest part and if that completed the next natural step is to create a custom onion address, it's not mandatory and you can pick a random one but let's spice things up a bit by generating a new private key. One of the most pupular tools to generate a custom onion address is a software called Eschalot, the one we will be using today.
Open a terminal and start with this commands :
~$ git clone https://github.com/ReclaimYourPrivacy/eschalot
Cloning into 'eschalot'...
remote: Enumerating objects: 4, done.
remote: Counting objects: 100% (4/4), done.
remote: Compressing objects: 100% (4/4), done.
remote: Total 86 (delta 0), reused 1 (delta 0), pack-reused 82
Receiving objects: 100% (86/86), 513.40 KiB | 2.35 MiB/s, done.
Resolving deltas: 100% (37/37), done.
~/eschalot$ ./eschalot -vct4 -p null
4 is the core numbers we want to put to work and null is the first characters we want our onion service to start with, for example : simpleonionwwdlsa20efdssd2.onion.
Once the tool generated the domain you wanted, you can use it for your hidden service.